With the rapid expansion of the internet and web technologies, web applications have become integral to our daily lives. These web apps process enormous amounts of sensitive data, making them a prime target for cyber criminals. As a result, ensuring secure user access and permissions management in web applications is not just desirable but crucial for any web development company.
In this blog, we’ll delve deep into the world of web application security, focusing specifically on the secure management of user access and permissions.
Best Practices for Secure User Access Management
As we delve deeper into web application security, one critical area that demands our attention is User Access Management. Securely managing user access isn’t just about setting up passwords; it’s a nuanced process involving a series of best practices to ensure that the right people have access at the right time.
This section walks you through some of the best secure user access management practices. We’ll cover everything from creating strong authentication protocols to implementing Single Sign-On (SSO) and regular auditing of unauthorized access privileges.
Whether you’re a seasoned IT professional or a startup founder looking to enhance your application’s security, these practices will guide you toward building a more secure and resilient system. So, let’s dive in and explore the world of secure user access management.
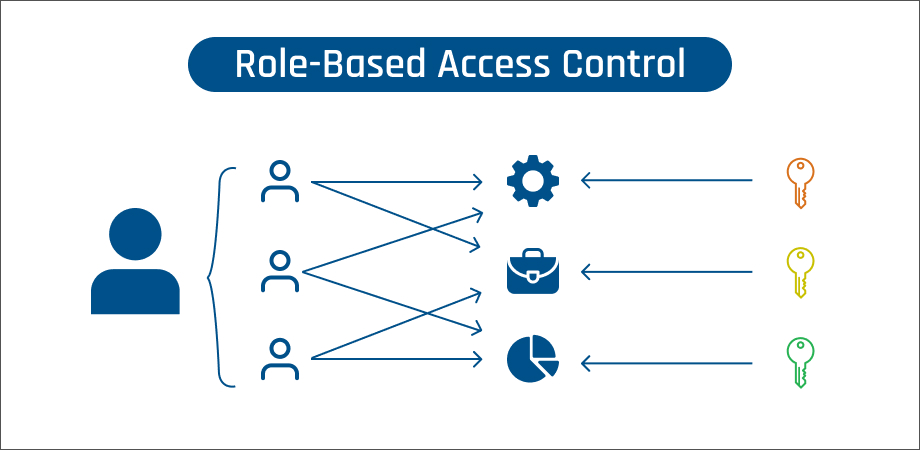
1. Role-Based Access Control (RBAC)
Imagine you’re part of a school theater production. Your production is like a web application; everyone involved has different roles and responsibilities. The play’s director, like the administrator of a web application, oversees everything. They make critical decisions, guide the overall vision, and have the ultimate authority on what happens on and off the stage. They can access all areas, from the script to the props and lighting system.
Then you have the actors. They are like regular individual users in the application. The actors have specific roles and scripts to follow. They can influence their performances, but they can’t change other actors’ lines or decide to change the web design. In the web application, regular users can interact with the areas relevant to their tasks but can’t alter fundamental features.
Lastly, imagine the audience members. They’re like guest users in a web application. They’re essential to the play because who would watch the performance without them? But can they jump on stage and join the performance? Can they access the backstage area? No. They can view the play and enjoy the performance, but they can’t make changes or give a level of access to restricted areas.
Role-Based Access Control, like our school play, ensures everyone gets to play their part but also that they don’t overstep their bounds. It’s about giving every user the exact permissions they need – no more or less. This makes the web application both a secure and harmonious place, just like our play being both an enjoyable and orderly experience. So, we create a safe, efficient, and well-coordinated digital environment through RBAC where everyone knows their role and sticks to it.
2. Email / OTP or Pre – Authorization ( Multi-factor authentication )
Think of multi-factor authentication as a super secure locker at school. Now, imagine if you had two or even three instead of just one lock on that locker. That’s what multi-factor authentication does. It adds an extra layer of security, making it much harder for anyone else to get in.
You use something you know for the first lock, like your locker combination. This is like your normal password for a web application. Let’s say you open that lock, but instead of getting into your locker, you find a second lock. This time, it’s a lock requiring a special key only you have. This might be a unique code sent to your email or phone in the digital world. This code is called a One-Time Password (OTP) because it changes whenever you want to unlock it.
Sometimes, there might even be a third lock. This could be something you only have, like a special ID card, or something unique about you, like your fingerprint. This is the ‘pre-authorization’ part.
So, why is multi-factor authentication so important? Let’s say someone discovers your locker combination (or your password). They could open your locker and get your stuff if that was the only lock. But with two or three locks, they’d also need your special key and maybe even your ID card or fingerprint. That’s a lot harder to get!
That’s why multi-factor authentication makes you feel safer, like when you know your stuff is secure in your locker. And it also makes logical sense because it’s much harder for a bad guy to break through several layers of security. So, it’s like having a super secure locker for your digital life, keeping your information safe and giving you peace of mind.
3. Centralized Access Control
Imagine you’re in a large school with several buildings – the science lab, library, art room, etc. Now, each of these buildings has a gatekeeper who decides who can enter and who can’t. It sounds a bit chaotic, doesn’t it? What if the gatekeeper of the science lab allows someone who should only be in the library?
Centralized Access Control is like having one main gatekeeper for the entire school. This gatekeeper has a list of who is allowed to go where. So, when you show up, the gatekeeper checks the list and says, “Okay, you’re allowed in the science lab and the library, but not the art room.” This makes things much simpler and more secure, right?
In a web application, Centralized Access Control is the “main gatekeeper.” It’s a single system that manages all user access and permissions. When a user tries to access a part of the application, this system checks if they can do so.
Having Centralized Access Control is like knowing one responsible person is keeping the school safe. It gives you a sense of security and order. And logically, it makes sense too. It’s easier to manage and less likely for mistakes to happen because there’s just one system, or “gatekeeper,” to update and maintain. So, whether you’re a student moving between buildings or a user navigating a web application, Centralized Access Control ensures that everyone is in the right place, providing safety and efficiency.
4. Password Management System
Imagine you have a bunch of keys – one for your house, one for your bike, another for your locker at school, and so on. It’s a lot to keep track of, right? And what if you lose one or forget which key is for which lock? That’s where a key ring comes in handy. It keeps all your keys in one place, neatly organized, and easy to find.
A Password Management System is like a digital key ring for all your passwords. It keeps all your passwords secure and organized in one place, so you don’t have to remember them all. You only need to remember one super secure password that unlocks your Password Management System, or in our case, your key ring.
But why is this so important for web application security? Well, it’s because people often reuse the same password for different sites or choose simple passwords that are easy to guess. It’s like using the same key for every lock – if someone finds that key, they can open all your locks!
A Password Management System encourages using unique, complex passwords for each site. It’s like having a different, highly secure key for every lock. And you don’t have to worry about remembering them all because your digital key ring takes care of that.
So, using a Password Management System gives you peace of mind, knowing that your keys (or passwords) are all safe and organized. And from a logical point of view, it makes sense. It’s easier and more secure to manage many passwords this way. So, just like a key ring for your keys, a Password Management System is a must-have tool for managing your passwords securely.
5. Attribute-Based Access Control (ABAC)
Imagine you’re at a music concert. There are different areas like the stage, backstage, audience area, and VIP section. Now, who can go where isn’t based on their role (like a performer, crew member, audience, or VIP) but also on certain attributes or characteristics.
For instance, only performers on the current set list can be on stage. Crew members can access backstage only during their assigned shift times. VIPs can enter the VIP section only if they have a special wristband. This is how ABAC works. It controls access based on various attributes, not just the user’s role.
In a web application, ABAC looks at multiple factors or attributes. These could be the user’s role, location, time of day, the sensitivity of the data they’re trying to access, and so on. For example, an employee might be able to view sensitive data while at the office during work hours but not when they’re using their laptop at a coffee shop after work.
ABAC makes a web application feel like a well-organized concert. It gives you the comfort of knowing that everyone is where they should be. And it makes sense too. By considering various attributes, it provides flexible and fine-grained access control, ensuring higher security. So, whether enjoying a concert or navigating a web application, ABAC ensures a secure, orderly, and personalized experience for everyone.
6. Separation Of Access Logic and Business Logic
Let’s imagine you’re at a theme park. Now, the theme park is divided into two main parts: the entrance gate, where tickets are checked, and the rides and attractions, which are the heart of the park.
Just as the entrance gate in a theme park serves as an important checkpoint, in web development a web application’s ‘access logic’ performs a similar function. It checks if you have a valid ‘ticket’ – in other words, if you have the right credentials to enter or access the application. Like its theme park counterpart, this gatekeeper doesn’t concern itself with specific activities you might engage in once inside, such as what ‘rides’ you’re qualified for or what ‘food stalls you might visit. Its primary job is controlling admission – determining who gets in and who doesn’t.
On the other hand, the rides and attractions are like ‘business logic.’ They are the main reason people visit the theme park. Each ride has its own rules – you must be this tall to ride, you need a special ticket for certain attractions, etc.
These two parts – the entrance gate and the rides – must operate separately. Why? Because it keeps things organized and secure. The gatekeepers at the entrance shouldn’t have to worry about the rules for each ride, and the ride operators shouldn’t worry about checking tickets. Each has its job to do.
Similarly, in a web application, separating access logic (who can use the application) from business logic (what they can do within the application) keeps things tidy and secure. It’s a bit like having different people handle different tasks – it prevents confusion, makes the application easier to manage, and ensures tighter security.
So, whether you’re enjoying a day at a theme park or using a web application, separating tasks – or, in this case, access logic and business logic – ensures a smooth, enjoyable, and secure experience.
7. Ability to Audit User Activity
Picture yourself as a detective in a mystery game. You have a magnifying glass that lets you see footprints, fingerprints, and other clues. You can trace where each player has been and what they’ve done. By piecing these clues together, you can solve the mystery.
In web applications, the ability to audit user activity is like having that detective’s magnifying glass. It allows the system to record who did what, where, and when. For example, it can tell you that User A logged in at 2 PM and downloaded a specific file, or that User B deleted an item at 3 PM, and so forth.
Why is this important? Just like the detective feels reassured knowing they can find clues to solve the mystery, having an audit trail gives you a sense of security. It’s comforting to know that if something unusual happens, you can trace back the steps and discover what led to it.
From a logical perspective, it’s a no-brainer too. It allows for accountability because users know their actions are being tracked. It also helps in diagnosing and solving issues. For instance, if a piece of data gets lost or modified, you can look at the audit trail to find out who last accessed or changed that data.
So, whether you’re unraveling a mystery in a game or managing a web application, the ability to audit user activity is a powerful tool that brings both a sense of security and a practical way to track and solve issues.
8. Front-end vs Back-end Access Control
Think about a popular restaurant. The restaurant has two main areas: the dining area (or the “frontend”), where customers enjoy their meals, and the kitchen (or the “backend”), where the chefs prepare the food.
Customers in the dining area can view the menu, place orders, and eat their food. This is like the front end of a web application, where users can see and interact with the interface. Access control in the front might involve hiding certain menu options from users who aren’t logged in or showing admin options only to users with admin privileges.
On the other hand, customers usually don’t have access to the kitchen, right? The kitchen is where the chefs work magic, using their special recipes to create delicious dishes. This is like the backend of a web application, where the data is stored and processed. Backend access control is all about who can access this data and what they can do with it. For instance, a user’s identity might be able to view their order history but not that of other users.
You feel at ease when you’re at the restaurant, knowing that not just anyone can wander into the kitchen. It adds to the enjoyment of your meal. And it just makes sense, right? The chefs have their workspace, and you have yours. Both are important, but they’re protected in different ways.
Similarly, it’s crucial to have both frontend and backend access controls in place in web applications. This ensures that users can only see and do what they’re supposed to, whether browsing through the menu (the front end) or digging into their personal orders (the back end). It’s like the harmony between a restaurant’s dining area and kitchen, creating a secure and enjoyable experience for everyone.
9. Access Control Policies and Guidelines
Imagine you’re playing a board game like Monopoly. Before you start the game, you first read the rulebook, right? The rulebook tells you what each player can and cannot do. It decides who can buy properties, how much money each player starts with, and what happens when you land on someone else’s property. These rules make the game fair and enjoyable for everyone.
Similarly, in web applications, access control policies and guidelines are like the game’s rulebook. They set the rules for what each user can and cannot do. For example, they might say that only admins can delete users, that users can only view their own profile, or that customer data can only be viewed from the office, not from public places.
Having these policies gives you the same feeling of fairness and order when playing a board game with clear rules. You know everyone is playing by the same rulebook, which makes you feel secure and confident.
From a logical perspective, these policies and guidelines are essential for maintaining order and preventing application misuse. By defining clear rules, they ensure everyone knows their roles and responsibilities. They also make it easier to manage and monitor user access, much like how the rules of a board game guide the players and keep the game on track.
So, whether you’re rolling the dice in Monopoly or logging into a web application, clear rules – or, in this case, access control policies and guidelines – are key to a secure, fair, and enjoyable experience.
10. OWASP Recommendations
Imagine you’re planning a hiking trip. It’s a big, exciting adventure but also a bit scary because you’re not sure what to expect. So, you decide to hire an experienced guide. The guide gives you a list of do’s and don’ts to ensure your safety during the hike. Having this advice makes you feel safer and more confident about your adventure.
In web applications, the Open Web Application Security Project (OWASP) acts like that experienced guide for your hiking trip. OWASP is an online community that provides free information about web application security. One of their best-known resources is the OWASP Top Ten, a list of the most critical web application security risks and how to prevent them.
For example, one of the risks on the OWASP Top Ten is “Broken Access Control.” This means a user might be able to access data or functions they shouldn’t be able to. To prevent this, OWASP recommends limiting the number of unsuccessful logins attempts a user can make or ensuring that users can only access their data, not someone else’s.
Just like how you’d feel more secure and confident on your hiking trip with a guide’s advice, following OWASP recommendations can give you a sense of security when building or using a web application.
And from a logical perspective, these recommendations are backed by a large community of security experts. They’re based on real-world data about the most common and dangerous security issues. So, it’s like having a guide who’s led hundreds of hikes and knows exactly what to watch out for.
So, just like that guide on your hiking trip, OWASP can help you navigate the challenging terrain of web application security. With their recommendations in hand, you can embark on your journey confidently, knowing you’re prepared to handle whatever comes your way.
11. Single Sign-On (SSO)
Have you ever visited a theme park where you get a wristband at the entrance, which lets you ride all the rides without needing a separate ticket for each one? It’s pretty cool, right? You feel like you have a magic key to the park, making your experience much smoother and more enjoyable.
Single Sign-On, or SSO, works kind of like that wristband. When you log into a web application using SSO, you enter your username and password once. After that, SSO lets you access multiple related services without logging in again. It’s as if you have a magic key that lets you open many doors instead of carrying a separate key for each one.
From a logical perspective, SSO isn’t just convenient. It’s also a secure way to manage user access. Remembering one strong password is easier than remembering many, so users are less likely to write down their passwords or forget them. SSO can also reduce the risk of phishing since users aren’t constantly entering their credentials.
But it’s not just about logic. There’s also a feeling of freedom and ease that comes with using SSO. Like that wristband at the theme park lets you enjoy your day without worrying about tickets, SSO lets you navigate different services smoothly and securely. It feels like you’re being taken care of, making your online experience much better.
So, Single Sign-On is like a magic key or an all-access wristband, making your online journey both secure and enjoyable. It’s one of the best practices for managing user access and permissions in web applications, and it’s easy to see why.
Conclusion:
In our digital journey, we’ve explored how to manage user access and permissions in web applications securely. We’ve learned that it’s not just about setting up a system and hoping for the best. It’s about implementing effective strategies like Role-Based Access Control, Multi-factor Authentication, and Centralized Access Control.
Think of these strategies as a digital castle’s walls, gates, and guards, keeping the valuable treasures – our data – safe from unwanted intruders. We’ve learned that user access management is not a one-size-fits-all endeavor, but rather it requires a tailored approach, much like crafting a perfect outfit or cooking a delicious meal from a well-thought-out recipe.
From the simplicity and convenience of Single Sign-On to the well-informed guidelines from OWASP, these techniques are our allies in maintaining a safe and secure digital environment. They serve not only the logical need for security but also evoke a feeling of confidence and peace of mind, just like knowing your home is safe when you leave for a vacation.
Just as a responsible hiker respects the guidelines from an experienced guide or a good chef who follows a trusted recipe, effectively managing user access and permissions in web applications involves understanding and implementing these best practices. These tools and techniques are about keeping intruders out and enhancing the user experience, making our digital journey smoother and more enjoyable.
Are you ready to take your web application’s security to the next level? Our team specializes in securely managing user access and permissions. Contact us for expert guidance and services tailored to your specific needs. Your web application security is our priority.